Implementing a firewall in the correct place is important. Discover where most organizations choose to place theirs.


Firewalls are an essential component of networks and their placement matters. Logically, a firewall is placed between the internet service provider (ISP) and the local area network (LAN) devices. As traffic passes through the firewall monitors that traffic against a set of predetermined rules and controls the access to the network. A firewall functionalities help business networks to prevent hackers from stealing data and also stop the spread of malware and denial-of-service (DoS) attacks.
See below to learn all about popular firewall placements and the importance of selecting the best location for them.
Traditionally, firewalls are inserted inline across a network connection and monitor incoming or outgoing traffic. They help to separate the different networks based on a set of predefined rules, which ensure access control between the networks. Firewalls perform at several network segments of the organization networks. As a perimeter defense, a firewall is positioned between networks with different security levels and generally controls traffic between the external networks and internal networks or external networks and demilitarized zone (DMZ) networks, or even between internal networks.
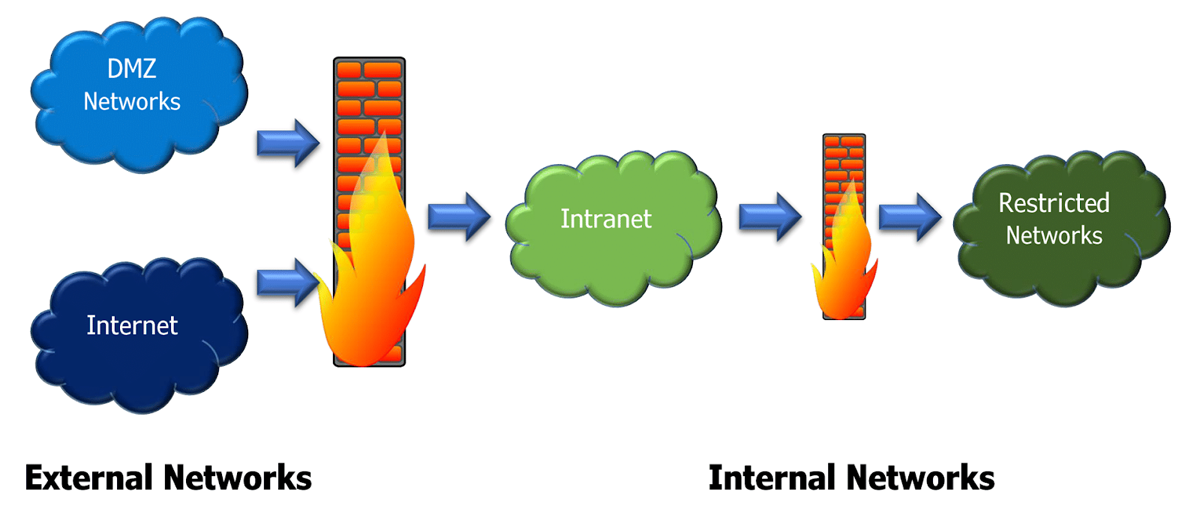
According to the organization’s network environment and security requirements, a single firewall can cover all enforcement points simultaneously. Multiple firewalls can be used in multi-layer deployment for both physical interfaces (layer 2) and physical interfaces (layer 3). The most basic configuration is a wide area network (WAN) connected to a router, then a firewall filters each traffic and distributes it into the network.
Some firewall placements for a large enterprise to personal use are given below.
Enterprise firewall configurations are a bit more complicated compared to consumer-grade firewalls. The firewalls run on a dedicated machine in the network and placement of a business firewall within network topology is more important. The firewall should be connected to the WAN, DMZ, and company network. To ensure more security they may use a configuration with two firewalls. Where the first firewall is placed after the outermost device that connects to the WAN and passes traffic to the DMZ network, and then, a second firewall receives internal traffic pass through the DMZ into the internal network. Larger businesses implement multiple firewalls in their network that allows the creation of a variety of “zones” of varying access levels.
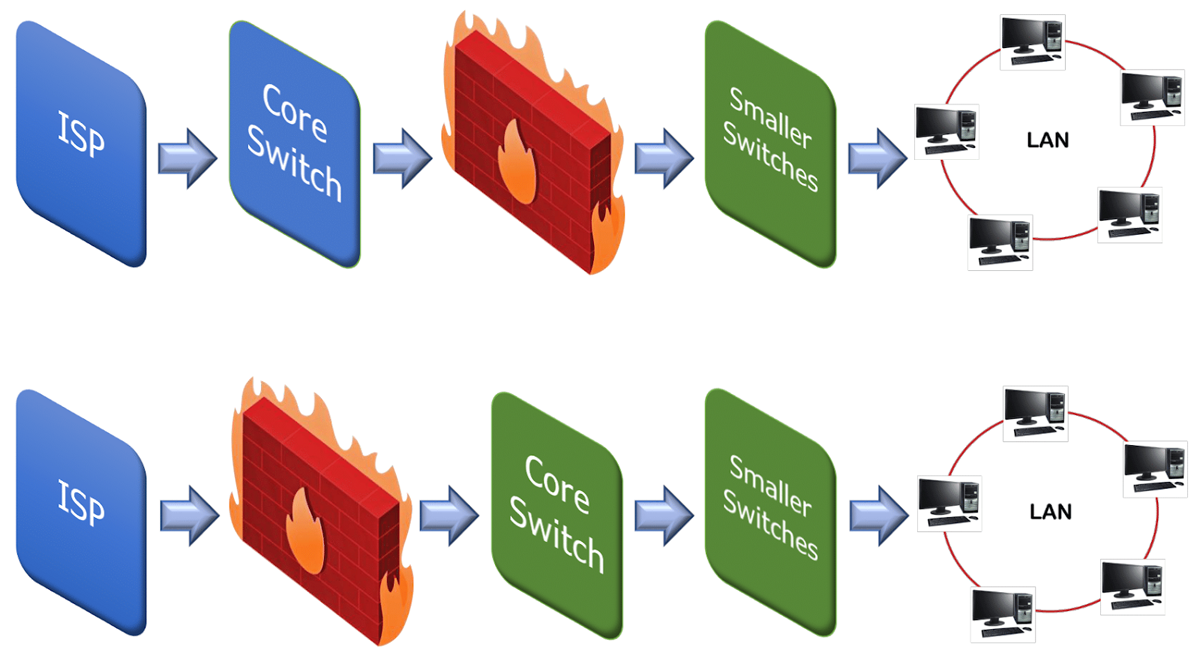
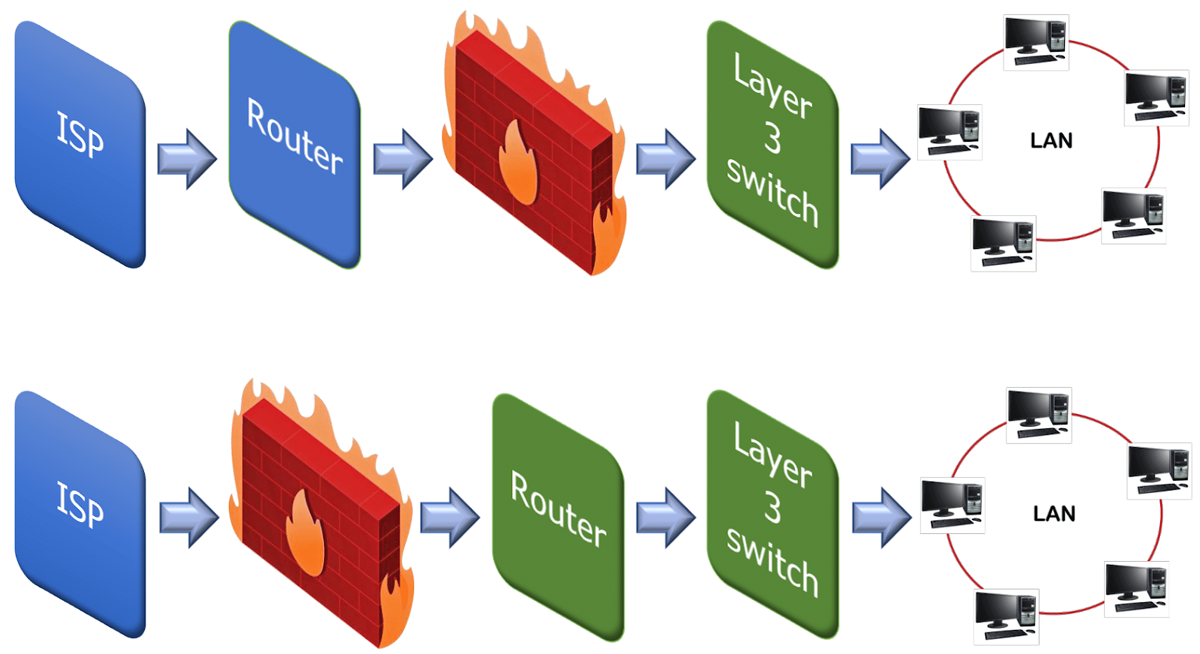
The firewall resides on the network’s locations just before the traffic enters the router, which is known as the ingress point. Sometimes the firewall co-resides with the router, but placing the firewall after the router is rare for a multipath node because the firewall device must follow each of the multiple egress paths. Most hardware firewall devices contain router capabilities. In switched networks, a firewall is often part of the switch to enable protection of the switched segments. The onboard firewall features of a router can perform an additional security operation before sending it to the firewall. Companies may deploy a router with firewall features (router with firewall capability), or they can deploy a firewall device connected to the network (or a firewall device).
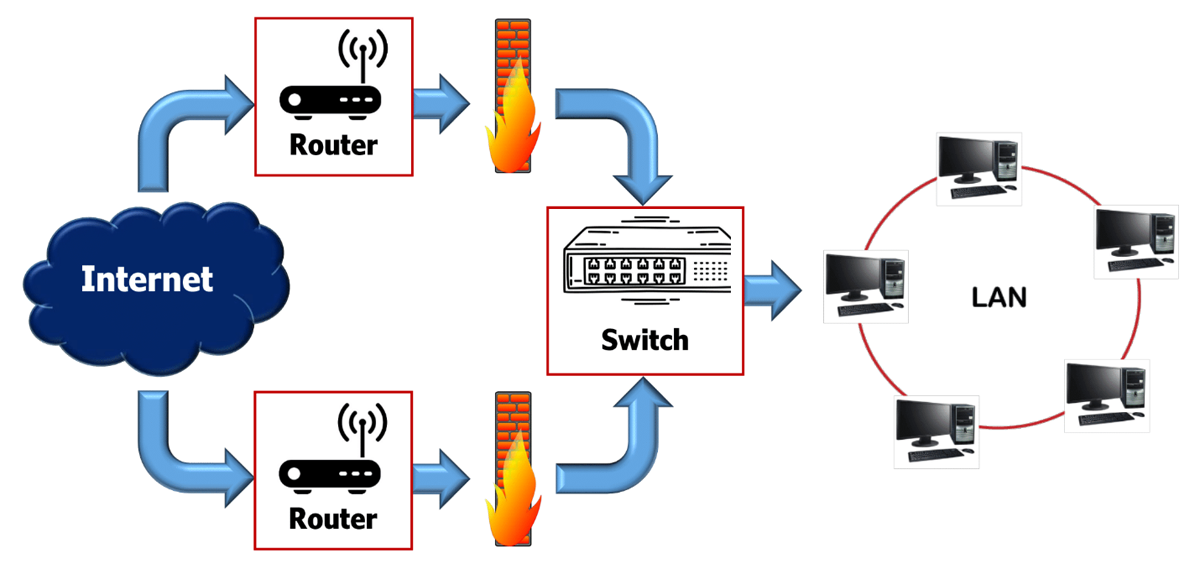
Parallel firewall placement helps to provide greater performance improvements for large networks. If enterprises host their website on their own network, a firewall will enable outside traffic to and from the website servers but will block unauthorized incoming or outgoing traffic through the internal computers based on the basis of security rules. The systems with parallel firewalls may consist of a load balancer and a firewall array, where each firewall in the array is identical. When a data packet arrives it will be sent to one of the firewalls in the array and the load balancer maintains short packet queues.
Read more: 7 Different Types of Firewalls & Deployment Options Explained
The right placement and proper configuration of the firewall are directly related to its performance, resource utilization, and threat prevention.
To ensure the complete cybersecurity of a system it is important to maximize the performance of the firewall for incoming and outgoing traffic. Firewall performance depends on the position where it is placed. By adjusting settings and mitigating the impact of DoS attacks, firewalls can help business continuity to ensure security even during a major cyberattack. Companies can create a DMZ, or a zone with the right setup within the business network; the DMZ may contain public-facing services such as mail, FTP, VoIP servers, as well as the business website. The right configurations of the firewall deliver complete protection by monitoring the trends and patterns in traffic.
At the network-level gateways, the firewalls inspect the headers of each network packet to determine where the packet is coming from and its destination. They have excellent performance and consume few resources. At the application-level gateways, more complex firewalls analyze each content of packets with the header and effectively filter packets and control access to resources by analyzing the protocols. Stateful inspection firewalls analyze traffic at multiple levels of the network and can prevent a wider array of threats but they’re also resource-intensive. The firewall should be placed in the right positions, otherwise, some of the resources can be wasted or the system can be flooded by DoS attacks.
Generally, a firewall is not designed to scale to the huge number of connections per second (CPS), and it deals with every unique flow according to zone, IP, protocol, and application. So firewall placement plays a critical role to avoid the flooding of counters for DoS attacks. To ensure the best protection against DoS attacks should place the firewalls as close to the resources as possible, which will reduce the session numbers the firewall may handle. Do not place the firewalls in front of dedicated devices and allow those high-volume devices at the first line of defense to mitigate the flood of DoS attacks.
Firewalls are a necessary part of network security, helping to prevent harmful access to data and resources. Placing a firewall in the right position in the network ensures the safe and efficient use of the system’s resources.
Many cybersecurity vendors are offering different types of firewalls with state-of-the-art technology and rich functionality. These firewalls provide a deeper level of protection with easy placement and setup. Different types of firewalls are used for different purposes, it is important to place the firewall as per your system requirements so it can run very efficiently. The system with proper firewall configuration and placement has greater control over the network traffic and delivers complete protection of business data against today’s advanced security threats.
Learn more about firewalls in this guide.


Al Mahmud Al Mamun is a writer for TechnologyAdvice. He earned his B.S. in computer science and engineering from Prime University, Bangladesh. He attained more than 25 diploma courses and 100 certificate courses. His expertise and research interests include artificial intelligence (AI), artificial neural networks, and convolutional neural networks.

Enterprise Storage Forum offers practical information on data storage and protection from several different perspectives: hardware, software, on-premises services and cloud services. It also includes storage security and deep looks into various storage technologies, including object storage and modern parallel file systems. ESF is an ideal website for enterprise storage admins, CTOs and storage architects to reference in order to stay informed about the latest products, services and trends in the storage industry.
Property of TechnologyAdvice. © 2026 TechnologyAdvice. All Rights Reserved
Advertiser Disclosure: Some of the products that appear on this site are from companies from which TechnologyAdvice receives compensation. This compensation may impact how and where products appear on this site including, for example, the order in which they appear. TechnologyAdvice does not include all companies or all types of products available in the marketplace.