Data storage security is a segment of the cybersecurity field specifically focused on protecting data and storage infrastructure against unauthorized disclosure, modification, or destruction, and assuring the data is only accessible to authorized users. This takes many forms, and a successful data storage security strategy includes hardware, software, risk assessments, administrative controls, and policy components. This article provides an overview of data storage security and how it fits in with data protection and DevSecOps, and looks at storage security vulnerabilities and key drivers in the data storage security field.
What is Data Storage Security?
The Storage Networking Industry Association (SNIA) Dictionary describes data storage security as “the application of physical, technical, and administrative controls to protect storage systems and infrastructure as well as the data stored within them.” Putting this into practice requires a careful balancing act involving three primary concerns: confidentiality, integrity, and availability.
Each of these concerns creates tension with the others. For example, locking down systems to keep sensitive data out of the hands of unauthorized users and ensure that the data is reliable can also make it more difficult for everyone in the organization to access the data when they need it. Security measures might put an additional burden on users, but it shouldn’t be so ominous that they seek ways around it—they work best when they have buy-in from the staff members affected by them..
The goal is to build strong enough security systems that breaching them would require potential attackers to expend more time and resources than the data would ultimately be worth. But you also need to be aware of costs and how they measure up against the value of the data so you’re not building data storage security systems that are more expensive than the value of what they are protecting.
Data Storage Security Vulnerabilities
Risk is inherent in any technology, and malicious actors are always finding new ways to exploit vulnerabilities. Storage devices are vulnerable in a number of ways, whether they’re cloud-based, networked, or on-premises.
Lack of encryption
While some high-end network attached storage (NAS) and storage area network (SAN) devices include automatic encryption, many storage products on the market require organizations to install separate software or an encryption appliance in order to make sure that their data is encrypted.
Cloud storage
Although some argue that cloud storage is more secure than on-premises storage, the cloud adds complexity to storage environments and often requires storage personnel to learn new tools and implement new procedures in order to ensure that data is adequately secured.
Incomplete data destruction
When data is deleted from a hard drive or other storage media, traces may be left behind. It’s up to storage administrators and managers to ensure that any data erased from storage is overwritten so that it cannot be recovered.
Weak physical security
Some organizations don’t pay enough attention to the physical security of their storage devices. In some cases they fail to consider that an insider, like an employee or a member of a cleaning crew, might be able to access physical storage devices and extract data, bypassing all the carefully planned network-based security measures.
Data storage security involves identifying these and other vulnerabilities and mitigating the risk associated with them, keeping the data secure, accessible, and available.
Data Security, Data Protection, and DevSecOps
Data security is closely related to data protection. The former primarily involves keeping private information out of the hands of anyone not authorized to see it. It also includes protecting data from other risks, such as ransomware that prevents access to information or attacks that alter data, making it unreliable.
Data protection, on the other hand, is more focused on making sure data remains available after non-malicious incidents like system or component failures or natural disasters.
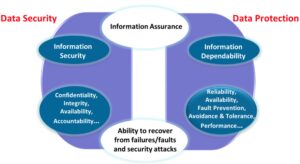
Where the two overlap is in their shared desire to ensure the reliability and availability of information and to recover from any incidents that might threaten an organization’s data. Storage professionals often find themselves dealing with data security and data protection issues at the same time. Many of the same best practices can help address both concerns.
Data security and data protection are clearly overlapping concerns. Image Source: SNIA
Within the IT field, data storage and cybersecurity were traditionally separate disciplines with occasionally overlapping concerns. That model is changing. As the cybersecurity risk continues to grow, threatening nearly all sectors of industry and touching more and more business functions across each enterprise, many IT teams are adopting a DevSecOps approach that holds everyone in the organization responsible for security.
As more companies adopt DevOps—a practice combining the traditionally separate development and operations teams and processes to unify the development, deployment, and maintenance of software through rapid and continuous updates—their approach to security has changed, too. DevOps integrates application building with security. This includes secure storage.
DevSecOps takes the idea a step further, integrating security into application development and deployment and spreading responsibility for security throughout the organization. How and what that contribution looks like will vary across departments and roles, but for storage professionals it means paying greater attention to data storage security—and for organizations, it means adopting a more holistic approach to IT that ensures the active inclusion of the storage team.
Key Data Storage Security Drivers
While much of data security is driven by need—a number of high-profile data breaches have reinforced the imperative of vigilance—several recent trends have also increased enterprise interest.
Data Growth and Value
As enterprises increasingly rely on data for business intelligence, consumer engagement, and competitive analysis, the sheer volume of data is expanding relentlessly. Organizational awareness of data value is on the rise—but for data to be useful, it must be trustworthy and of highest quality. Storage is relatively cheap, and enterprises can readily add it internally or provision it in the cloud—but data storage security becomes a greater challenge as storage volumes grow. That means investing in security systems and secure storage to prevent data compromise.
Cost of Breaches
There were more than 35 million known cyberattacks around the world in 2022, and we’re on track for even more in 2023. They’ll cost organizations over $8 trillion globally this year, according to experts. Those expenses can be a powerful encouragement to improve data security.
Edge Computing
Because enterprises are moving more data to edge facilities and to the cloud, storage and other IT assets must be focused on new strategies to prevent unauthorized access to data and storage media that reside outside of traditional data centers.
Regulation
Governments are taking an increasing interest in data security and passing stronger laws as a result. The European Union’s General Data Protection Regulation (GDPR) has forced companies around the world to take stronger measures to protect customer privacy. This affects storage security as well.
Business Continuity
The U.S. experienced 18 separate weather and climate disasters that cost more than $1 billion each in 2022. Disastrous weather conditions have continued in 2023. Collectively these events have made disaster recovery and business continuity top of mind in corporate boardrooms, driving demand for secure backup and other storage security technologies.
Bottom Line: Data Storage Security
Enterprises have notably begun to recognize the need for cybersecurity measures in all aspects of their work, including where and how they store their data—which increasingly is becoming one of the most valuable assets of any organization. Stored data is vulnerable to threats ranging from the accidental deletion of files by employees to natural disasters that wipe out storage devices to malicious attacks from hackers.
Data storage security is the practice of identifying and mitigating those threats while keeping the data available, accessible, and reliable to the people who need it—and secure from those who should not have access to it. While there are different approaches to data storage security, the general process involves finding the balance between security and accessibility while keeping abreast of evolving threats. It’s just one part of an enterprise security posture—but as the value of data to business practices grows, it’s rapidly becoming one of the most critical.
Read next: 12 Data Storage Security Best Practices