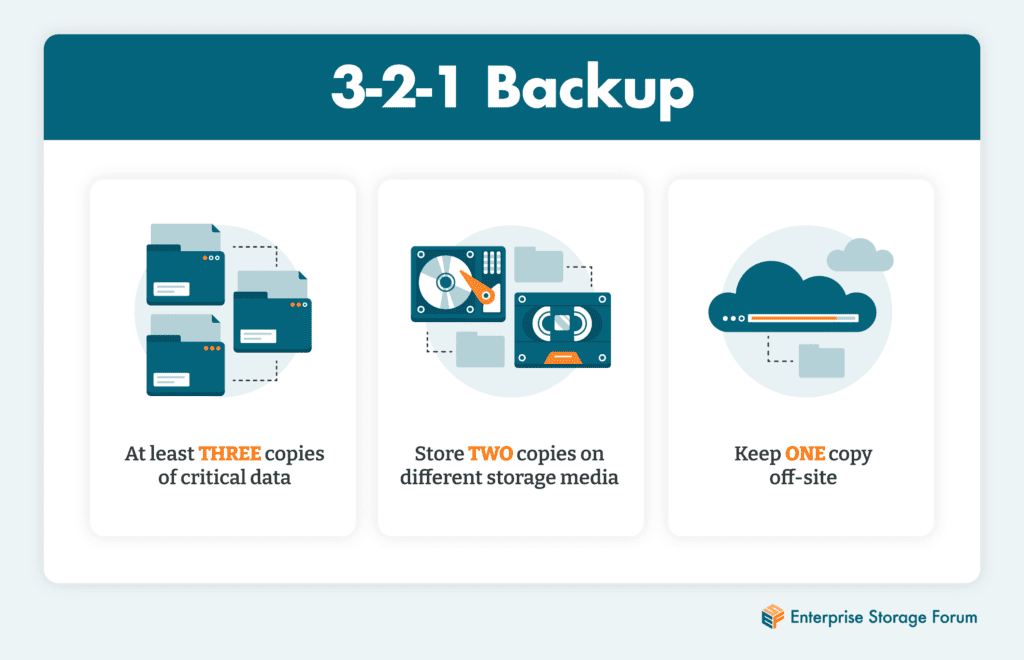
The 3-2-1 backup rule is a time-honored best practice that recommends keeping three copies of critical data—the original plus two backup copies—each stored on a different media, with one kept off site. It’s been the standard in data protection for decades, but is it still relevant in the cloud era? This article unpacks the 3-2-1 backup rule and makes recommendations for how enterprises can replicate the benefits and security it brought to their data in the context of today’s complex storage solutions.
Jump to:
- How Does the 3-2-1 Backup Rule Work?
- Why is the 3-2-1 Backup Rule Important?
- Is the 3-2-1 Backup Rule Still Relevant?
- 3-2-1 Backup Pros and Cons
- Bottom Line: Ensuring Reliability With 3-2-1 Backup
How Does the 3-2-1 Backup Rule Work?
The 3-2-1 backup rule has long been a popular strategy for backing up mission critical data. In the early days of computing, it meant keeping the original copy on an on-premises server with the other two copies—backups kept on tape—split between on- and off-site locations. But the concept has evolved over time to keep pace with new technologies.
For example, some businesses keep one of the backup copies on disk or on a deduplication appliance, some keep one on disk and another in the cloud, while others still store backups on two different clouds—with the same provider, shared between two providers, or in a public and a private cloud.
Which is to say that the clearcut definition of the original 3-2-1 backup rule has grayed with age. But what has not changed is the essential best practice at the heart of it: three copies, two different media, one stored offsite.
Why is the 3-2-1 Backup Rule Important?
Backing up important data is the baseline. But having a copy is not enough to guarantee its safety. Risk is rampant—drives fail, people make mistakes and delete files, natural disasters can flood offices. Buildings burn down. People steal things. Keeping a backup copy of data in the same location or on the same storage media mitigates its usefulness if something goes wrong.
The 3-2-1 pattern evolved over time as the best way to ensure that copies of organizational data are always to hand for operational recovery. Done correctly, 3-2-1 means that in the event of an outage or disaster, IT can turn to its backup files for a reliable copy of enterprise data.
3-2-1 Backup and Cybersecurity
In recent years, 3-2-1 has taken on added importance because of the increased threat of cyberattack. Good backups stored securely provide a very real line of defense against cyber threats. Backups stored on-site can be corrupted or infected by ransomware or other malware.
Is it enough to keep a backup copy or two in the cloud? Probably not—any cyberattacker who can get into enterprise systems might also be able to quietly infect all systems connected to the internet. More than a few companies have restored their files from backups only to find that they reintroduced the ransomware into their environment in the process—or worse, that their backups had also been encrypted or corrupted.
The best approach for a secure and recoverable backup is to keep one copy on tape, which can be stored offsite. This “air gapped” backup—one not connected to the internet—can be used to recover from digital or physical theft, with no network connection over which to introduce malware.
Is the 3-2-1 Backup Rule Still Relevant?
No longer the simple system it once was, the 3-2-1 backup rule now encompasses many possible configurations—but the concept remains as relevant as ever, even as it evolves to fit the realities of the cloud and the needs of modern data placement.
Cloud providers offer a form of all-cloud 3-2-1 in which customers store everything on a high-performance cloud tier, keep another copy in a lower tier, and a third copy in a cold storage tier. Smart enterprises split such functions among cloud providers for redundancy.
Modern clouds offer security features such as encryption, key management, embedded hashes and checksums to fight against data corruption and misuse, immutability courtesy of erasure coding and write once/read many (WORM) properties that provide a barrier against ransomware and other malware. WORM functionality embedded into backup software can be used by administrators when content is passed to the end media, whether that is cloud or on tape.
Tape continues holding its own as a good home for large amounts of archived material, making it a solid choice for large enterprises using 3-2-1 backup. Beyond a petabyte or so, its cost-effectiveness makes it hard to justify keeping huge amounts of data on disk—and the latest systems can feed data from offline tape cartridges to production systems within a few minutes. It’s worth noting that major cloud providers are among the biggest users of tape, which they often use to provide customers with the lowest tiers of cloud storage.
3-2-1 Backup Rule Pros and Cons
There are many advantages to the 3-2-1 backup rule:
- For operational recovery, keeping backups on-premises and stored on high-performance disk or SSDs is a good way to meet stringent recovery point objectives (RPOs) and recovery time objectives (RTOs).
- For long-term retention, the cloud can either store an entire copy of all data or act as a virtual substitute for a secondary data center.
- An air-gapped copy of data on tape provides heightened security and protection against ransomware.
There are disadvantages, too—here are the most common:
- 3-2-1 incurs cost—it requires more disk and solid state drive (SSD) space, tape systems, and additional cloud resources, as well as IT staff time.
- Some organizations have to deploy data reduction technology to reduce the cost of backup storage, both on-premises and in the cloud.
- It can be slow to retrieve data from offsite backups.
- Cloud data recovery can be expensive and overwhelm the network.
- Backups are vulnerable and must be protected using encryption in-flight and at-rest, ransomware protection, and other safeguards.
Bottom Line: Ensuring Reliability With 3-2-1 Backup
Backup technology does not stand still. The software, hardware, and cloud services available today have reshaped the entire backup and recovery discipline, and with it, the 3-2-1 approach. Such innovations as Virtual Tape Library (VTL), replication, deduplication, compression, multi-tenancy, snapshots, automation, and software-defined storage help businesses provide more rapid data backup and recovery than ever before, as well as enhanced security.
There are a great many excellent providers of enterprise-class backup services available today. Backup-as-a-Service (BaaS) providers can now take care of the entire backup management and administration function for businesses using the public cloud, an internal private cloud, or a managed service provider cloud. It can even take place inside the organization, with backup jobs run by tenants within portions of the IT infrastructure.
Innovations will continue to reshape 3-2-1 in the years ahead, but its basic philosophy is sound—and likely to stay with us for years to come.
To learn more about protecting mission-critical data, read our Guide to Selecting Backup and Recovery Software.



