Internet small computer systems interface, or iSCSI, is a storage area networking transport protocol that allows client devices to access block-level storage devices over an Ethernet network. Like Fibre Channel, iSCSI can be used for storage area networks (SANs) and works on shared networks or dedicated storage networks. It cannot, however, support file access solutions like network attached storage (NAS) or object storage solutions, which use different transport protocols. This article explains how the iSCSI protocol works and the benefits and limitations of using it.
Table of Contents
How Does iSCSI Work?
In a storage area network, or SAN—an independent high-speed network of connected switches, hosts, and storage devices—the iSCSI protocol is used to transmit data over the Ethernet network that connects users to the storage devices. iSCSI functions in the transport layer. It makes it possible for network connected devices to appear local to users.
A data packet, or unit of data bundled together for network transit, is made up of the data payload and a header that stores information about the packet, including destination and origin IP addresses. It’s also called a datagram. A data unit in the TCP transport layer is called a segment, and a data unit in the link layer is called a frame.
When an end user application initiates a request to the operating system, an appropriate SCSI command and data request are generated. A packet header is added to the request and encapsulated as a protocol data unit (PDU) containing SCSI data inside the TCP header as part of an Ethernet frame. The entire frame is then transmitted over the Ethernet network.
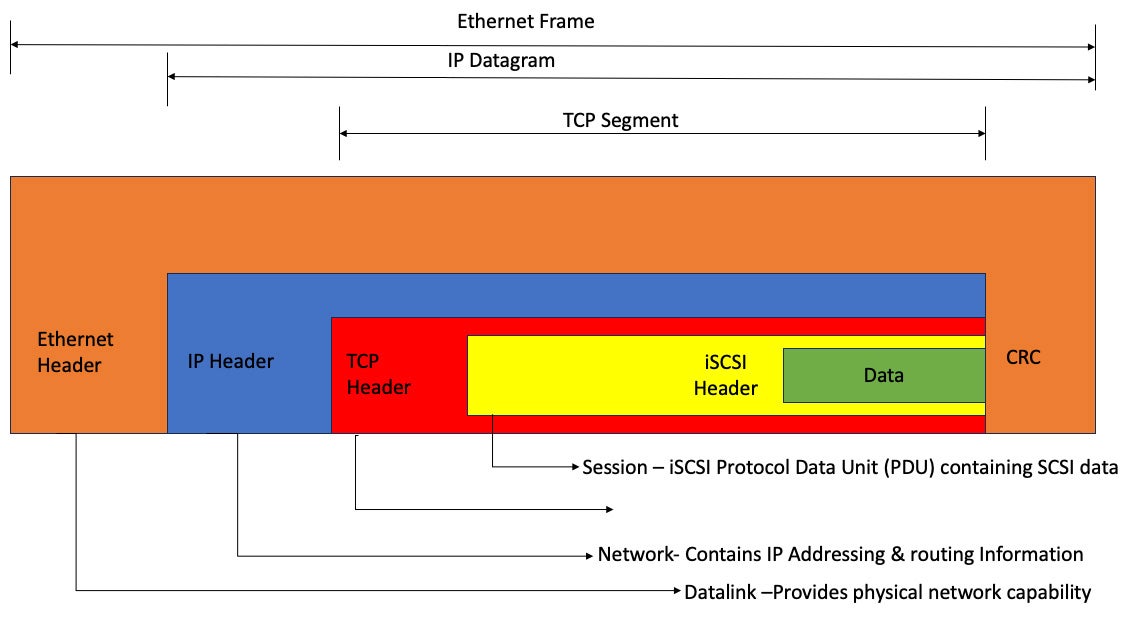
When the Ethernet frame reaches its final destination, the target datalink layer removes the frame encapsulation and sends the results to the network. The iSCSI protocol disassembles the packets and separates the SCSI commands, allowing the operating system to see the storage device as a locally connected SCSI device.
The SCSI commands are sent to a SCSI controller, and the controller diverts those SCSI commands to the SCSI storage device. The iSCSI protocol is bi-directional and can also return data in response to the original request.
The iSCSI protocol uses iSCSI initiators and iSCSI targets. The PDU depicted in Figure 1 communicates between the initiator and the target. The information in the PDU helps establish a session, transport iSCSI commands, move data, and provide node detection information.
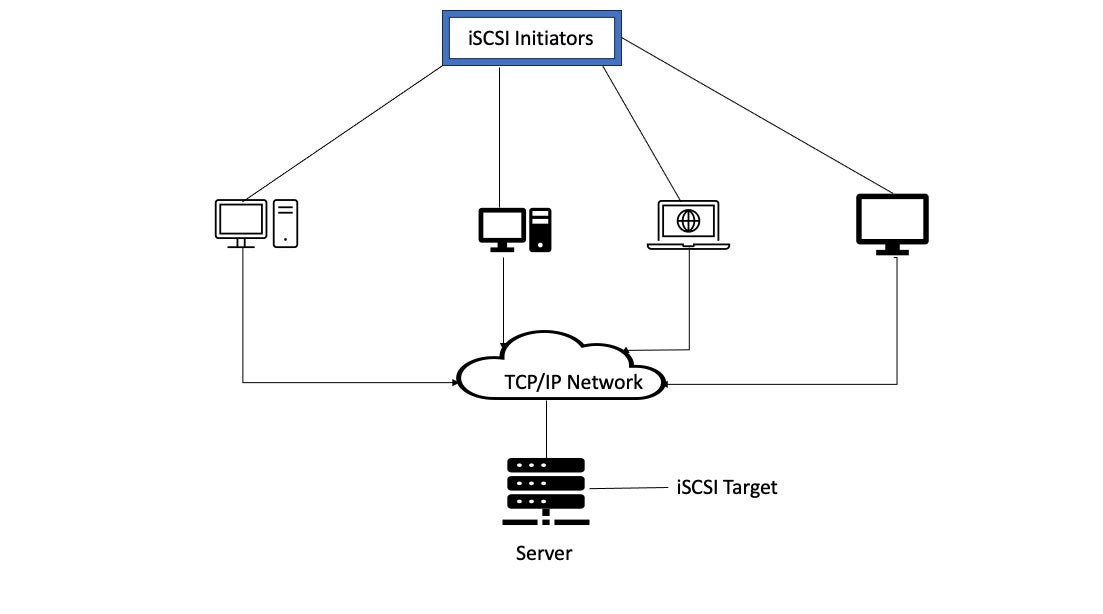
The initiator resides on the client machine. It can be initiated by either software or hardware, but software initiation is much more common. Servers are the iSCSI target and can receive initiator requests on one or more TCP/IP connections.
iSCSI Performance
Because the iSCSI network and protocol can transmit data over local area networks, wide area networks, and the Internet, the performance of an iSCSI network varies greatly depending upon variable factors, including the speed of the network and storage controller and the controller configuration.
Ethernet switches and media can operate at speeds of 1 GB, 10 GB, 40 GB, and 100 GB. iSCSI network speed is usually configured for 10 GBs infrastructure networks.
iSCSI vs. Fibre Channel: Storage Data Transmission Methods
iSCSI and Fibre Channel (FC) are both effective and popular for transferring a large amount of data. The following chart shows the major differences between iSCSI and FC.
| iSCSI | Fiber Channel | |
|---|---|---|
| Infrastructure | The same infrastructure is deployed in the user and server network | Dedicated infrastructure separated user and server network |
| CPU Load | Higher than Fiber Channel | Lower than iSCSI |
| Supported Distance | Distance is not limited | Limited distance |
| Deployment | Easy to manage and simple | Labor-intensive and complex |
| Latency | Higher than Fiber Channel | Lower than iSCSI |
| Cost | Less Expensive | More Expensive |
| Applicability | Well-suitable for low input/output application | Well-suitable for high input/output application |
When to Choose iSCSI Over Fibre Channel
Fibre Channel SAN is great for businesses with enough budget and expertise to implement and manage a dedicated fiber channel network. iSCSI SANs run on Ethernet networks and do not always need dedicated network hardware. iSCSI SANs are good for businesses that require high-performance workloads without deploying dedicated network hardware.
Benefits of iSCSI
iSCSI offers a wide range of benefits for enterprises that deploy it as part of a SAN. Here are the most common:
- Built-in TOE. To eliminate the burden of additional processing on the host CPU, network interface cards (NICs) have built-in TCP offload engine (TOE) technology that offloads the TCP/IP stack processing to a network controller.
- Low initial investment. Businesses can keep their total cost of ownership (TCO) low by using an iSCSI protocol to access storage devices. In addition to the low TCO, the iSCSI creates a SAN that’s easy to install and requires minimal maintenance.
- No additional hardware required. The iSCSI uses the IP-based technology and interoperability of TCP/IP and the Ethernet without additional hardware.
- Additional security. iSCSI provides an extra layer of security to storage networks.
- Low training/maintenance costs. No additional training is required for network staff to use iSCSI protocol, and the increased storage usage without extensive oversight and management keeps operational costs down.
- High compatibility. Because IP is universal, non-proprietary technology that is globally used, different network storage equipment works seamlessly together.
- Flexible scalability. iSCSI SAN environments are easily deployed using existing network hardware and other devices, allowing businesses to expand storage capacity and scale as they grow.
- Low power consumption/cost. Lower infrastructure costs with fewer active switches online reduces infrastructure, power consumption, and cooling costs.
What are iSCSI Limitations?
Though iSCSI offers many benefits, like most technologies, it also has limitations. Here are the msot common:
- Conditional performance. When iSCSI technology is used in a mixed network that processes business data and iSCSI information, it creates higher latency and performance issues.
- Not SSD compatible. iSCSI uses serial technology, which means it’s not conducive to solid-state storage devices (SSDs).
- Limited capacity. The LUN maximum capacity of a hard disk drive is 250 TB, and the maximum capacity for NAS is 144 TB.
- Finite snapshots. There is a limit of 512 snapshots, or virtual copies of stored data, per iSCSI application and 64 for file share volumes. If the snapshot feature fails, data will be unrecoverable and the iSCSI performance will be negatively affected.
- Finite connections. iSCSI also has a maximum of 255 connections per session. If the session exceeds 255, the target will reject other concurrent connection attempts.
Bottom Line: iSCSI for Enterprise Solutions
The need for high speed data transfer and high capacity data storage have become essential to enterprise data functions. Storage area networks are a viable solution to both of these needs. SANs using the iSCSI protocol run on Ethernet networks, making them a good choice for businesses with existing networks that also require high-performance workloads but don’t want to purchase and install dedicated network hardware.
Read about the five types of enterprise data storage to learn more about the various ways businesses choose to store their data and make it accessible to users.



